Enterprise Tier Protection
Securing your business requires the comprehensive protection that enterprise security suites offer. By partnering with the same companies you do business with, Cylitic brings that protection to your small or medium business.
Whitepapers



Cyber threats are growing
The US National Cyber Security Alliance finds that 60% of small companies are unable to sustain their businesses over six months after a cyber attack.1
The average price for small businesses to clean up after a hack is $690,000; for middle market companies, it’s over $1,000,000.2
According to Osterman Research, more than half of all business impacted by a ransomware attack experience 9 or more hours of downtime.3
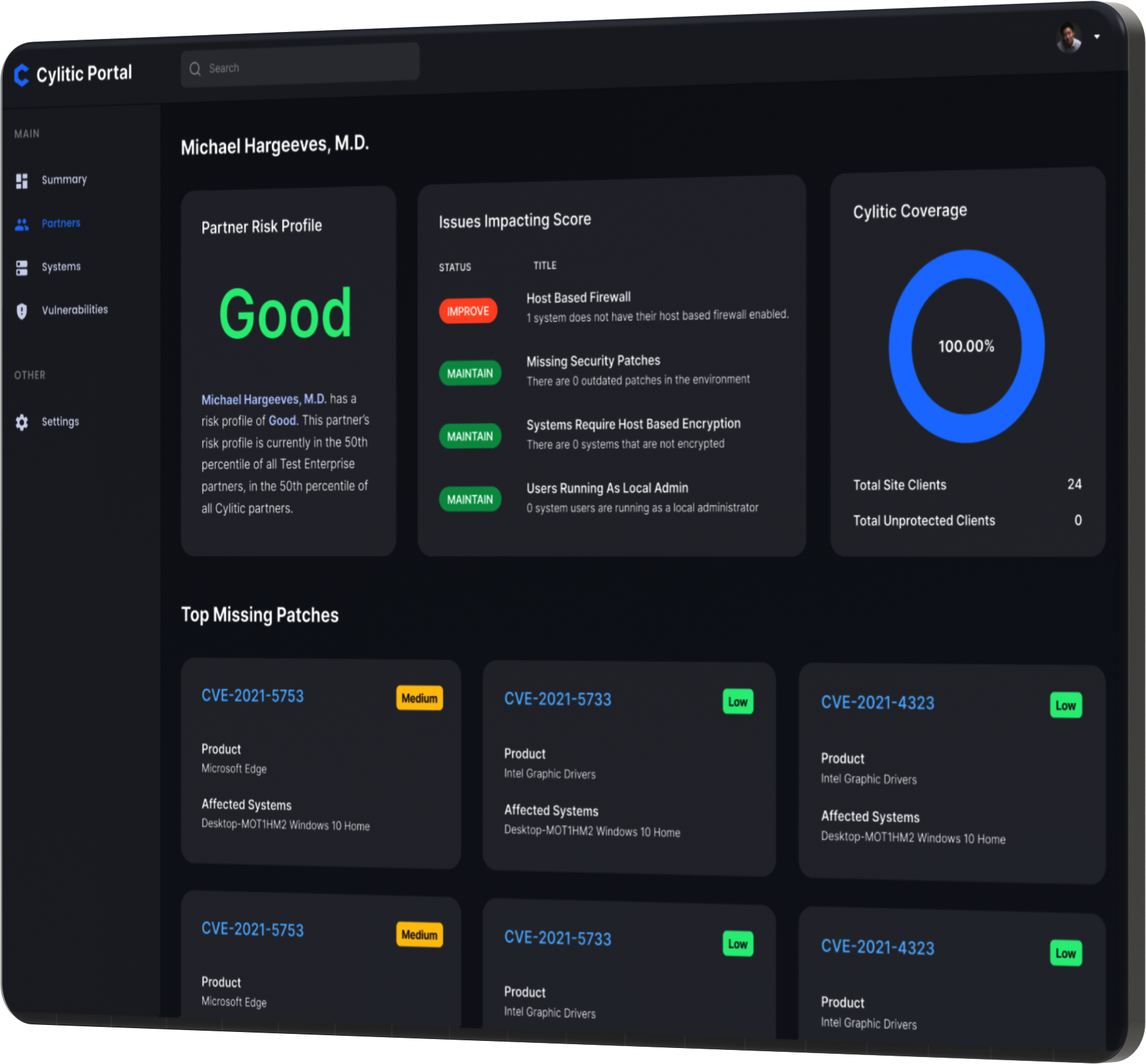
Reduce Risk
Managing today’s cyberthreat landscape is a full-time job. Most small and medium businesses do not have the resources, team, or expertise it takes to keep their company safe.
Cylitic takes care of your security so you can focus on your business.
Protect
Stop incidents before they happen with cutting-edge software and endpoint protection.
Respond
If something goes wrong, our incident response and breach support teams make it right.
Report
Certify and report your security compliance status, both internally and, if you choose, to your enterprise partners.
Defend Your Business
Cylitic leverages industry-leading expertise and top-grade software to keep your business safe from data breaches, ransomware, and other cyber attacks.
Our Partners




Jacki Monson
SVP, Chief Integration Officer, CISO & CPO at Sutter Health
CEO
Marketplace Company
IT Administrator
Software Company