 CyliticVueTM
CyliticVueTMReduce Risk. Maintain Trust.
Cylitic mitigates third party risk by protecting your partners’ systems, offering visibility into the security posture of those systems, and providing enterprise-level support to you and your partners if an incident occurs.




Safeguard Your Business Network
Monitoring and reinforcing the security of the third party partners you depend on takes the best tools and the best support. We have both.
 AI-Driven Malware Protection
AI-Driven Malware Protection Breach Support Services
Breach Support Services Cloud-Based DNS and HTTP(S) Filtering
Cloud-Based DNS and HTTP(S) Filtering Incident Response Expertise
Incident Response Expertise 24x7x365 Coverage
24x7x365 Coverage High-Level Visibility
High-Level Visibility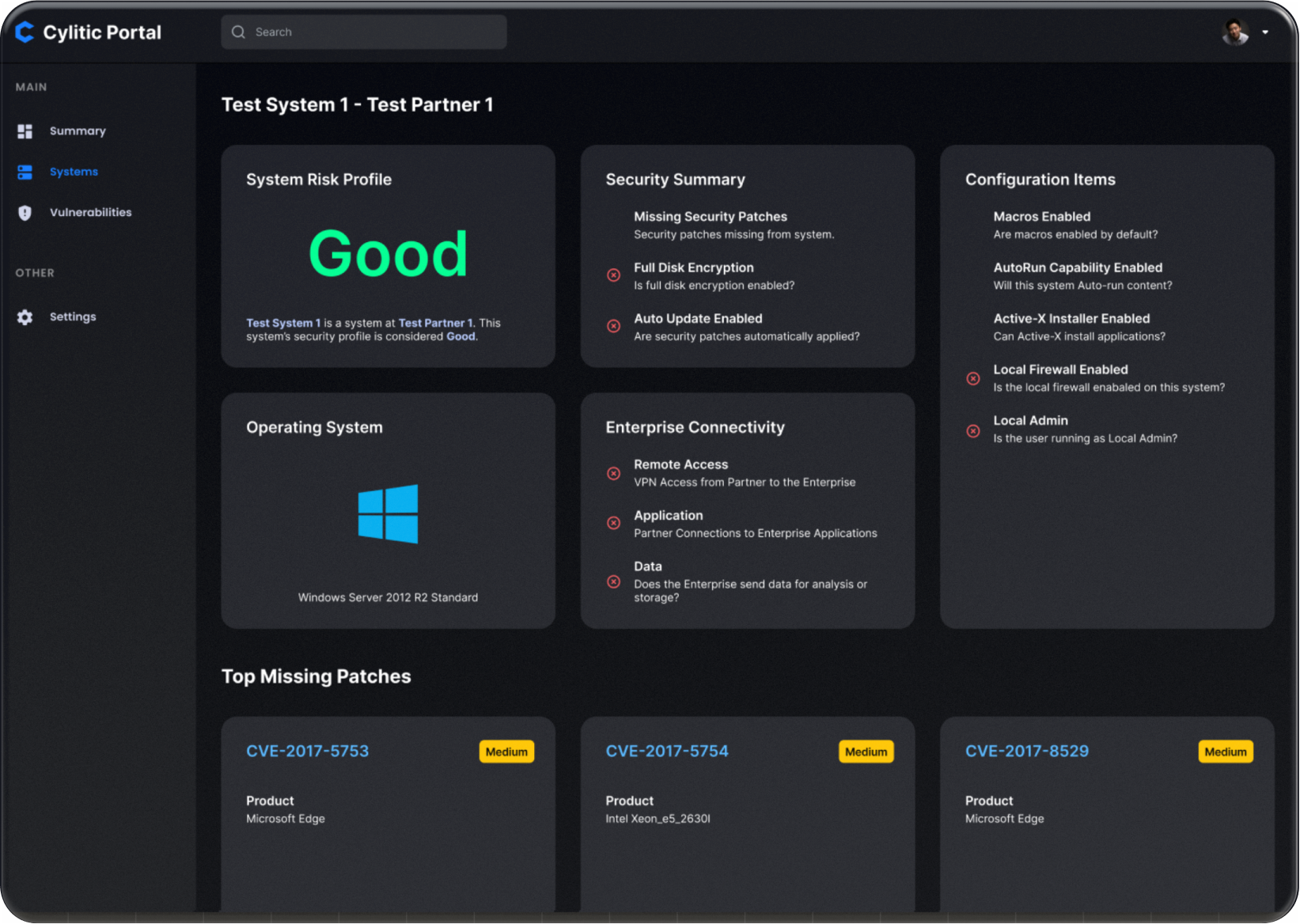
Risk Analysis
Quantify, verify, and fortify the security of your third party partners’ systems.
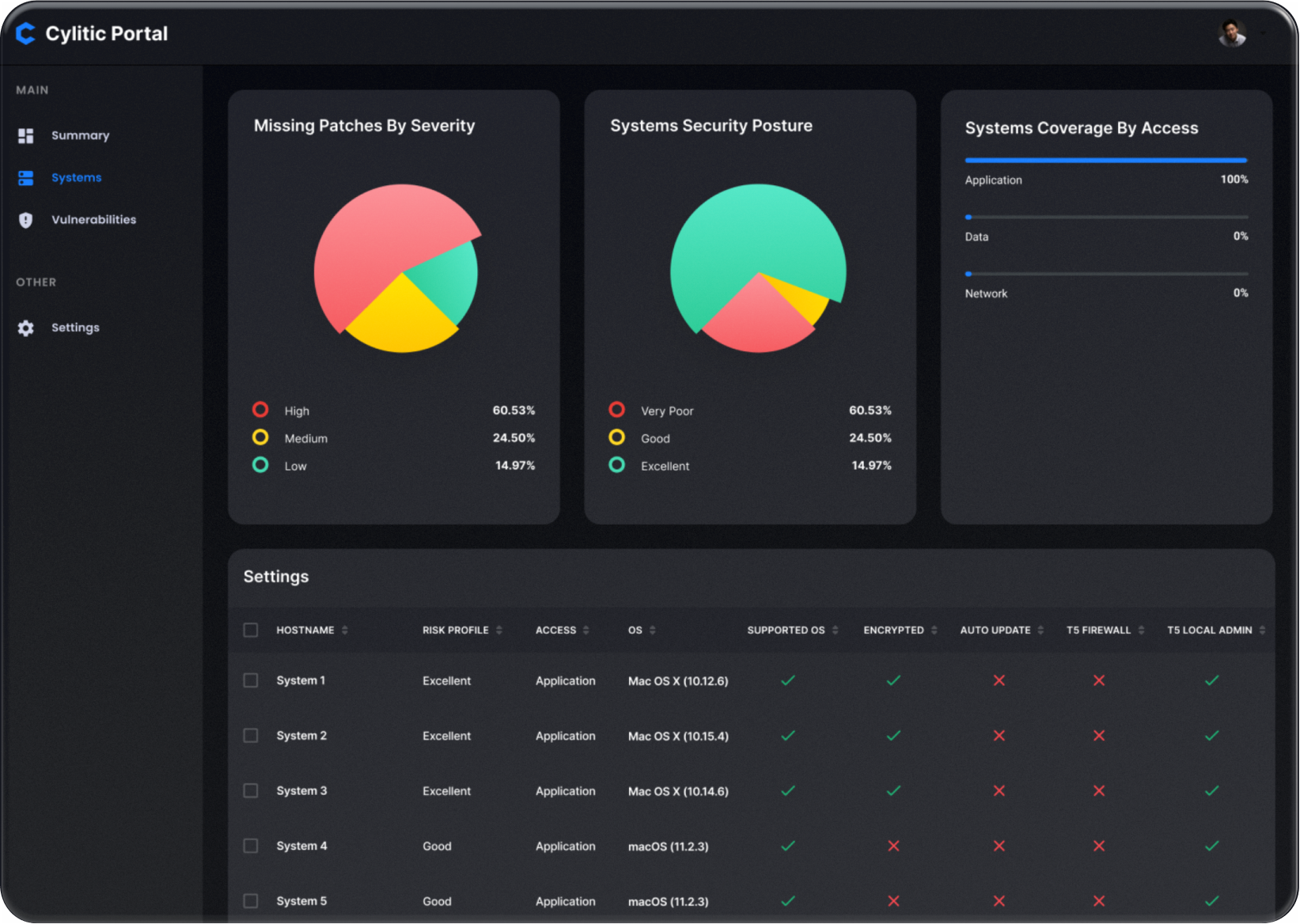
Continuous Detection & Response
Cylitic’s elite analysts perform threat hunting and response across your entire business network all day every day.
We record all security activity on protected systems so we can always determine whether your partner’s systems were compromised in the event of a cyberattack.
Enterprise-Level Visibility
Cylitic collects telemetry, alert, and incident information from your third party partners and reports it directly to you, automating the time-consuming process of monitoring compliance, quantifying remote technical risk at third party sites, and simplifying security compliance enforcement across your network.
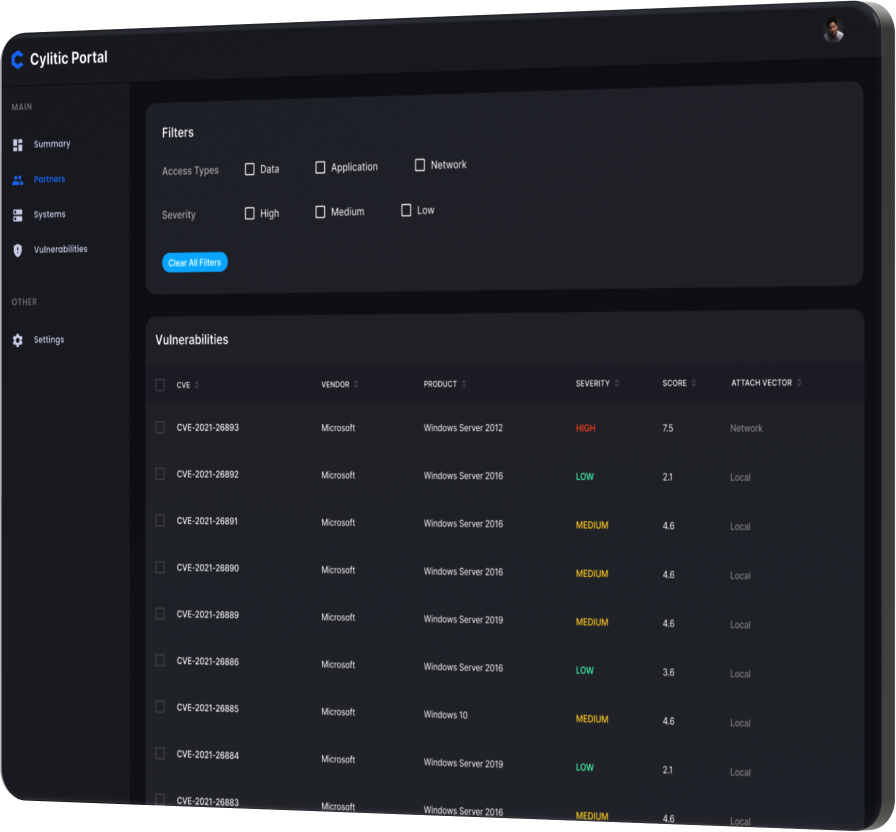
Risk Reduction
Stop incidents before they happen.
Next-Generation Protection
The Cylitic security stack installs with a single click on your partners’ systems and provides next-generation anti-virus protection, endpoint detection, response tooling, and network filtering using Cylance NGAV, Cisco Umbrella, and Tanium EDR.
While other anti-virus products rely on 30-year old technology only effective against known threats, Cylitic leverages machine learning algorithms trained to recognize malicious software even if it has never been seen before.
Endpoint Monitoring and Encryption
Lost or stolen devices are a leading cause of data exposure, and if those devices are unencrypted the data on them must be considered compromised – a difficult message to deliver to your regulators, customers, and consumers.
Cylitic monitors every endpoint, ensuring that every device with sensitive data is securely encrypted and letting you know if one is not.
Risk Response
If something goes wrong, we make it right.
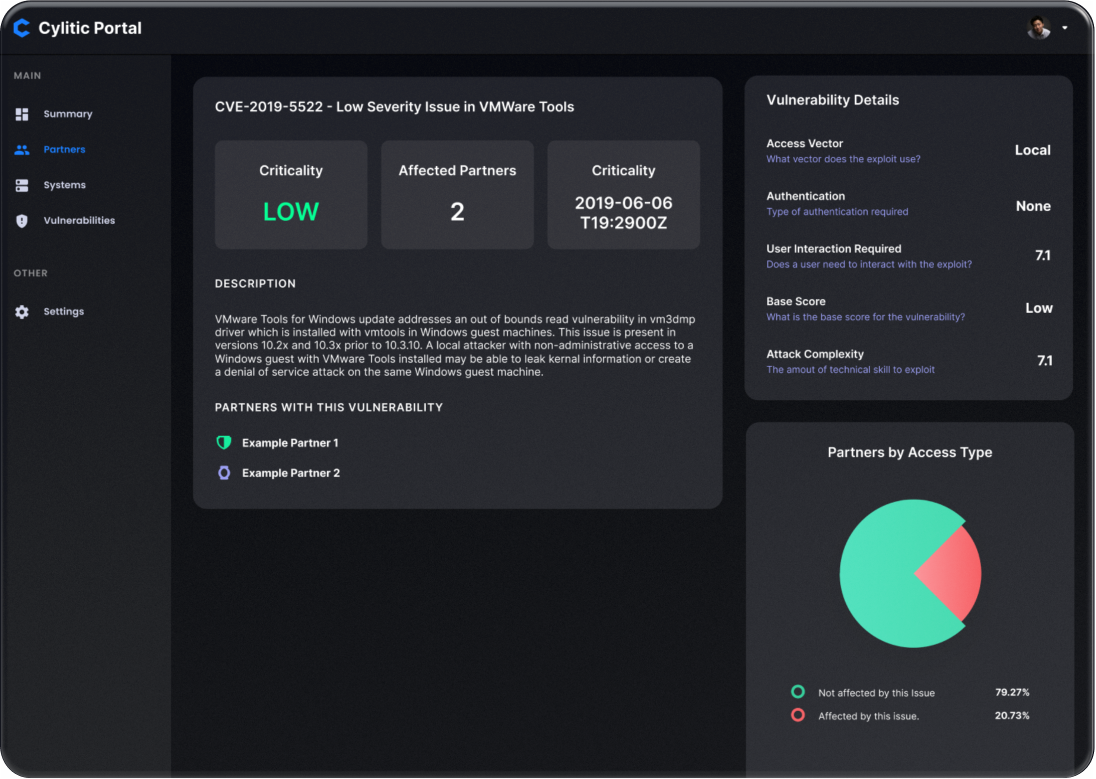
Breach Support
Risk can be mitigated; it can never be eliminated. Cylitic’s breach support services mean you’re covered even in the worst-case scenario. We can reduce your liability from data destruction, ransomware attacks, theft, hacking, and more.
Incident Response
If an incident does occur, Cylitic has the most comprehensive playbooks, the deepest connections, and the most sophisticated expertise to resolve it.